Cybersecurity researchers have uncovered multiple critical security vulnerabilities impacting the Versa Concerto network security and SD-WAN orchestration platform that could be exploited to take control of susceptible instances…. Continue reading
Tag: Attackers
SonicWall has released patches to address three security flaws affecting SMA 100 Secure Mobile Access (SMA) appliances that could be fashioned to result in remote code execution. The… Continue reading
Explore our in-depth Tier List of best Max Attackers to use in Pokémon GO’s Max Battles. Our Max Attackers Tier List is sorted into five categories, starting from… Continue reading
Cybersecurity researchers have shed light on a new campaign targeting WordPress sites that disguises the malware as a security plugin. The plugin, which goes by the name “WP-antymalwary-bot.php,”… Continue reading
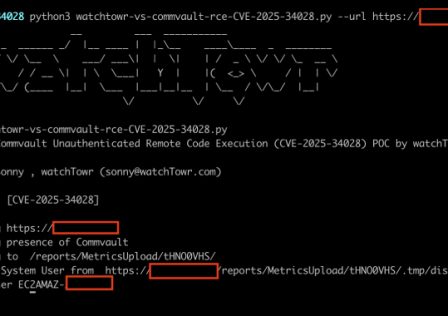
A critical security flaw has been disclosed in the Commvault Command Center that could allow arbitrary code execution on affected installations. The vulnerability, tracked as CVE-2025-34028, carries a… Continue reading
Cybersecurity researchers have detailed a now-patched vulnerability in Google Cloud Platform (GCP) that could have enabled an attacker to elevate their privileges in the Cloud Composer workflow orchestration… Continue reading
Fortinet Warns Attackers Retain FortiGate Access Post-Patching via SSL-VPN Symlink Exploit
Fortinet has revealed that threat actors have found a way to maintain read-only access to vulnerable FortiGate devices even after the initial access vector used to breach the… Continue reading
A maximum severity security vulnerability has been disclosed in Apache Parquet’s Java Library that, if successfully exploited, could allow a remote attacker to execute arbitrary code on susceptible… Continue reading
Critical Next.js Vulnerability Allows Attackers to Bypass Middleware Authorization Checks
A critical security flaw has been disclosed in the Next.js React framework that could be potentially exploited to bypass authorization checks under certain conditions. The vulnerability, tracked as… Continue reading
Cybersecurity researchers have disclosed details of two critical flaws impacting mySCADA myPRO, a Supervisory Control and Data Acquisition (SCADA) system used in operational technology (OT) environments, that could… Continue reading