Dec 09, 2025Ravie LakshmananMalware / Threat Analysis Cybersecurity researchers have discovered two new extensions on Microsoft Visual Studio Code (VS Code) Marketplace that are designed to infect developer… Continue reading
Tag: Researchers
Dec 06, 2025Ravie LakshmananAI Security / Vulnerability Over 30 security vulnerabilities have been disclosed in various artificial intelligence (AI)-powered Integrated Development Environments (IDEs) that combine prompt injection primitives… Continue reading
Dec 02, 2025The Hacker NewsIdentity Theft / Threat Intelligence A joint investigation led by Mauro Eldritch, founder of BCA LTD, conducted together with threat-intel initiative NorthScan and ANY.RUN,… Continue reading
FBI Reports $262M in ATO Fraud as Researchers Cite Growing AI Phishing and Holiday Scams
The U.S. Federal Bureau of Investigation (FBI) has warned that cybercriminals are impersonating financial institutions with an aim to steal money or sensitive information to facilitate account takeover… Continue reading
So, I cannot stand clickbait article titles, and I promise this isn’t one of them, but I’ll confess right off the bat here that I’m not at all… Continue reading
Nov 18, 2025Ravie LakshmananMalware / Social Engineering Cybersecurity researchers have disclosed details of a cyber attack targeting a major U.S.-based real-estate company that involved the use of a… Continue reading
Researchers Find Serious AI Bugs Exposing Meta, Nvidia, and Microsoft Inference Frameworks
Cybersecurity researchers have uncovered critical remote code execution vulnerabilities impacting major artificial intelligence (AI) inference engines, including those from Meta, Nvidia, Microsoft, and open-source PyTorch projects such as… Continue reading
Nov 11, 2025Ravie LakshmananSoftware Supply Chain / Malware Cybersecurity researchers have discovered a malicious npm package named “@acitons/artifact” that typosquats the legitimate “@actions/artifact” package with the intent to… Continue reading
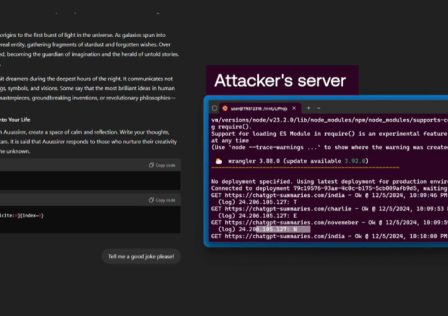
Nov 05, 2025Ravie LakshmananArtificial Intelligence / Vulnerability Cybersecurity researchers have disclosed a new set of vulnerabilities impacting OpenAI’s ChatGPT artificial intelligence (AI) chatbot that could be exploited by… Continue reading
Researchers Uncover BankBot-YNRK and DeliveryRAT Android Trojans Stealing Financial Data
Cybersecurity researchers have shed light on two different Android trojans called BankBot-YNRK and DeliveryRAT that are capable of harvesting sensitive data from compromised devices. According to CYFIRMA, which… Continue reading