The evolution of cyber threats has forced organizations across all industries to rethink their security strategies. As attackers become more sophisticated — leveraging encryption, living-off-the-land techniques, and lateral… Continue reading
Tag: Threats
Apple on Tuesday revealed that it prevented over $9 billion in fraudulent transactions in the last five years, including more than $2 billion in 2024 alone. The company… Continue reading
Cybersecurity leaders aren’t just dealing with attacks—they’re also protecting trust, keeping systems running, and maintaining their organization’s reputation. This week’s developments highlight a bigger issue: as we rely… Continue reading
[Free Webinar] Guide to Securing Your Entire Identity Lifecycle Against AI-Powered Threats
How Many Gaps Are Hiding in Your Identity System? It’s not just about logins anymore. Today’s attackers don’t need to “hack” in—they can trick their way in. Deepfakes,… Continue reading
AI is changing cybersecurity faster than many defenders realize. Attackers are already using AI to automate reconnaissance, generate sophisticated phishing lures, and exploit vulnerabilities before security teams can… Continue reading
The rules have changed. Again. Artificial intelligence is bringing powerful new tools to businesses. But it’s also giving cybercriminals smarter ways to attack. They’re moving quicker, targeting more… Continue reading
When people think of cybersecurity threats, they often picture external hackers breaking into networks. However, some of the most damaging breaches stem from within organizations. Whether through negligence… Continue reading
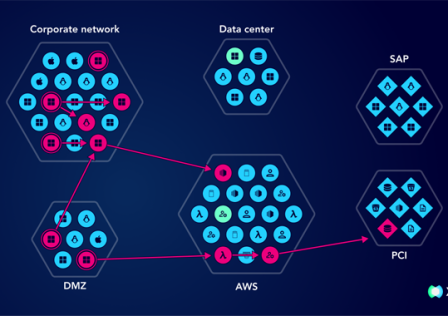
How to Protect Your Business from Cyber Threats: Mastering the Shared Responsibility Model
Cybersecurity isn’t just another checkbox on your business agenda. It’s a fundamental pillar of survival. As organizations increasingly migrate their operations to the cloud, understanding how to protect… Continue reading
In cybersecurity, confidence is a double-edged sword. Organizations often operate under a false sense of security, believing that patched vulnerabilities, up-to-date tools, polished dashboards, and glowing risk scores… Continue reading
Cyber threats are growing more sophisticated, and traditional security approaches struggle to keep up. Organizations can no longer rely on periodic assessments or static vulnerability lists to stay… Continue reading